Exploring the 3 Most Common Types of Cybersecurity
In today's rapidly evolving business landscape, the integration of new technologies is becoming ubiquitous. As these technologies become integral to daily operations, it is crucial for every employee to not only understand them but also be aware of the associated risks. Cybersecurity plays a pivotal role in safeguarding sensitive information and preventing cyberattacks that can target any company.
Unveiling Security Weaknesses Through Vulnerability Detection
Explore the significance of external perimeter scanning in uncovering and addressing security vulnerabilities before they become exploitable threats. Learn how this proactive approach enhances your website's overall cybersecurity.

Empowering Your Workforce: The Cornerstone of Cybersecurity with S-Checkup
The Role of Security Education
Security education encompasses a broad range of topics, from basic cyber hygiene to in-depth knowledge about advanced threats. It helps employees understand the importance of cybersecurity, the risks involved, and their role in protecting sensitive data. S-Checkup can provide tailored training programs that cover:
- Phishing Awareness: Recognizing and thwarting phishing attempts.
- Password Best Practices: Creating and managing strong, unique passwords.
- Data Handling: Safeguarding sensitive information and adhering to data protection regulations.
- Social Engineering: Identifying and defending against manipulation techniques employed by attackers.
- Device and Network Security: Safely connecting to networks and using company devices.

Enhancing Cybersecurity with the Zero Trust Security Framework
Understanding Zero Trust
Zero Trust is not just a concept; it's a holistic cybersecurity framework designed to protect your network from the inside out. The central premise of Zero Trust is straightforward: Trust no one, inside or outside your network, and always verify.
Traditional security models relied heavily on the perimeter defense strategy, assuming that once someone is inside the network, they can be trusted. Zero Trust, on the other hand, assumes that threats can exist both inside and outside the network, making continuous verification and monitoring essential.

Mastering Zero Trust Security: A Comprehensive Guide by S-Checkup
What is Zero Trust Security?
At its core, Zero Trust Security is a paradigm shift. It challenges the conventional notion that once inside the perimeter, entities are considered trusted. In the Zero Trust model, trust is never assumed. Instead, verification is continuously required for every user, device, and application attempting to access your network resources.

Zero Trust Model: A Modern Approach to Cybersecurity
Embracing the Zero Trust Philosophy
At the core of the Zero Trust Model lies a fundamental principle: "Never trust, always verify." Unlike conventional security models, Zero Trust challenges the assumption that entities within the network can be implicitly trusted. Instead, it emphasizes stringent verification of all users, devices, and applications seeking access to your network or resources, regardless of their location. This approach helps prevent unauthorized access, thereby reducing the risk of data breaches and lateral movement by cybercriminals.

Zero Trust Security Solutions: Building a Resilient Digital Defense
What Is Zero Trust Security?
Zero Trust is a security model founded on the principle of "never trust, always verify." It operates under the assumption that threats may already exist inside your network or are attempting to breach it. Instead of granting blanket access privileges based on location or user roles, Zero Trust enforces strict identity verification and least privilege access policies

The Evolution of Cybersecurity: Embracing Zero Trust Networking
Understanding Zero Trust Networking
Zero Trust Networking, often abbreviated as ZTN, is not just another security model; it's a comprehensive philosophy that challenges the long-standing concept of trusting everything within your network. At its core, Zero Trust follows the principle of "never trust, always verify." In simple terms, trust is never assumed; instead, rigorous verification is a prerequisite for all entities seeking network access.
Zero Trust Security Model: Fortifying Cybersecurity for Your Business
Understanding Zero Trust Security
Zero Trust is a cybersecurity framework that operates on the principle of "never trust, always verify." It assumes that threats can exist both inside and outside your network, and therefore, no entity should be implicitly trusted. Instead, Zero Trust demands rigorous verification of all users, devices, and applications attempting to access your network or data resources.
This model ensures that every access request is scrutinized, regardless of its source, and grants access only to authorized entities. It goes beyond traditional perimeter-based security and focuses on securing the core elements of your network, such as data, identity, and endpoints.

Shielding Your Small Business: Cybersecurity Essentials with S-Checkup
The Digital Threat Landscape for Small Businesses
Small businesses may think they're immune to cyberattacks, but the truth is, they are often seen as easier targets due to limited security measures. Here are some key threats:
1. Phishing Attacks
Cybercriminals use deceptive emails, messages, or websites to trick employees into revealing sensitive information or installing malware.
2. Ransomware
This malicious software encrypts your data and demands a ransom for its release, often crippling small businesses.
3. Insider Threats
Employees or contractors with access to your systems can inadvertently or intentionally compromise security.

Navigating Uncharted Waters: Overcoming OT Security Challenges with S-Checkup
The Landscape of OT Security
Operational Technology, which includes the machinery, devices, and control systems used in industrial settings, is undergoing rapid transformation due to the integration of digital technology. While this evolution brings unprecedented automation and efficiency, it also exposes OT environments to a host of security challenges.
Enhancing Your Website's Armor: The Power of Security Headers with S-Checkup
Understanding Security Headers
Security headers are essential components of web security that are transmitted by web servers to a user's browser. They provide instructions and guidelines for how the browser should interact with your website. Two critical security headers that are widely utilized are X-Content-Type-Options and X-Frame-Options.

Empowering Your Workforce: The Cornerstone of Cybersecurity with S-Checkup
Empowering your workforce through security education and training is an investment in the long-term security and success of your organization. At S-Checkup, we offer comprehensive cybersecurity services that include employee education and training. We understand that every organization has unique needs, which is why our programs are customized to align with your specific requirements.
Partnering with S-Checkup means that your organization will not only benefit from top-notch technology and expert guidance but also from a workforce that is well-prepared to protect your digital assets.

Mastering Security Incident Response: Safeguarding Your Business with S-Checkup
Understanding the Basics of Security Incident Response
Effective security incident response begins with preparation. Here are the fundamental steps every organization should consider:
1. Incident Detection
Proactive monitoring and detection are the first lines of defense. S-Checkup provides state-of-the-art threat detection systems to identify suspicious activities in real-time.
2. Containment
When an incident is detected, it's crucial to isolate the affected systems or networks swiftly. S-Checkup's experts will assist in containing the breach and minimizing the damage.
3. Eradication
After containment, our team will work to eliminate the root cause of the incident, ensuring that the vulnerability exploited is patched and removed.
4. Recovery
S-Checkup's cyber security services include robust recovery plans to get your operations back on track quickly.

Website Security Testing: Ensuring Your Digital Fort Knox
The Critical Need for Website Security Testing
Website security testing involves a series of evaluations and assessments to identify vulnerabilities, weaknesses, and potential entry points for cybercriminals. This process helps you maintain the integrity of your website and protect sensitive data.

Navigating Compliance and Privacy Regulations: Your Roadmap to Digital Trust
Embracing Compliance and Privacy Regulations
Compliance and privacy regulations are designed to protect individuals' and businesses' sensitive data, fostering trust in the digital realm. Understanding and adhering to these regulations is not just a legal requirement; it's a cornerstone of ethical digital conduct.

DDoS Mitigation: Protecting Your Digital Fortresses from Cyber Onslaughts
Understanding DDoS Attacks
DDoS attacks involve overwhelming a target website or online service with a massive volume of traffic. The goal is to flood the target's servers, causing them to become unresponsive and disrupting their online operations. These attacks can be financially crippling, damaging reputation, and causing substantial downtime.

Backup and Disaster Recovery: Safeguarding Your Digital Assets
The Essence of Backup and Disaster Recovery
Backup and disaster recovery (BDR) is a comprehensive strategy for protecting your digital data. It involves creating regular backups of your files and systems and having a plan in place to recover from unexpected events like data loss, hardware failure, or cyberattacks.

The Power of Regular Security Updates: Keeping Your Digital World Safe
The Significance of Regular Security Updates
Regular security updates are the foundation of a robust cybersecurity strategy. They address vulnerabilities, patch weaknesses, and ensure that your digital world remains resilient against an ever-evolving landscape of cyber threats.

Enhancing Online Visibility: Web Hosting Security Strategies for Improved Website Performance
Understanding Web Hosting Security
Web hosting security encompasses various measures and practices designed to protect your website and its data from potential threats. By addressing key security concerns, you can ensure a resilient and reliable online presence.

Choosing the Right CMS: WordPress, Drupal, or Joomla
Picture the boundless digital realm, where websites serve as your online persona. In this expansive landscape, CMS platforms like Drupal, WordPress, and Joomla act as the architects, shaping your virtual presence. However, the key to success isn't just creation but also safeguarding. In this article, we embark on a unique journey to explore these CMS giants and unlock the secrets of securing your digital dominion.
Website Security Guidelines: Protect Your Digital Presence with Expert Insights
In your quest for website security, consider the role of S-Checkup, your cybersecurity partner. S-Checkup offers advanced threat detection, security audits, incident response planning, and customized solutions to bolster your website's defenses. With S-Checkup by your side, you're not just protecting your digital fort; you're fortifying it with a formidable defense.

Mastering Content Security Policy (CSP)
Content Security Policy, often referred to as CSP, is a vital component of modern web security. It's a browser feature that helps protect web applications from XSS attacks and other code injection vulnerabilities. CSP works by defining a set of rules that dictate which resources a browser should load or execute on a given web page. By controlling the sources of content that can be displayed, CSP effectively mitigates the risk of unauthorized code execution.

Unlocking Digital Fortresses: SSL/TLS Certificates Demystified for Secure Online Success
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that establish secure communication channels over the internet. SSL/TLS certificates are digital credentials that facilitate this process. They are essentially small data files that bind a cryptographic key to an organization's details, verifying the legitimacy of a website or server. These certificates play a pivotal role in securing data transmission between a user's web browser and a server, preventing eavesdropping, data tampering, and other security threats.

Strengthening Your Defense: Protecting Against Cross-Site Scripting Attacks
The struggle to safeguard your digital domain continues in the broad cyberspace, where information flows nonstop. Cross-Site Scripting (XSS), a stealthy yet deadly threat hiding in the depths of the internet, is your tricky enemy. The power of validating and sanitizing user input is S-checkup's secret weapon against XSS attacks. We at S-checkup know that protecting your online castle demands dedication. #XXS #CyberSecurity #WebProtection

Enhancing Website Security: A Guide to User Authentication and Authorization
In the dynamic landscape of cybersecurity, two essential concepts stand as sentinels guarding the gates to your digital kingdom: user authentication and authorization. These concepts are the linchpin of secure online interactions, and in this article, we'll unveil the significance of each. By the end of this journey, you'll not only understand these vital components but also discover how S-Checkup can help fortify your digital fortress.

Unveiling the Power of APIs: Your Guide to Digital Security and Vulnerability Scanning Tools
APIs, or Application Programming Interfaces, serve as intermediaries that enable software applications to communicate and interact with each other. They define the methods and data formats that applications can use to request and exchange information, making them essential for the functioning of our digital world.

Securing Your Website: A Comprehensive Guide to Web Application Firewalls (WAFs)
Before delving into the protective prowess of S-Checkup's WAF, let's understand the enemy. Web application attacks, including Cross-Site Scripting (XSS), SQL Injection, and Distributed Denial of Service (DDoS), can cripple your online operations, tarnish your reputation, and result in financial losses.

Website security basics
The importance of a company's online presence has increased in the current digital era. The protection of these digital assets is crucial because websites are the main way that companies engage with their audience. As a result of the ongoing evolution of cybersecurity threats, it is essential for businesses to comprehend and put into practice the basic principles of website security:
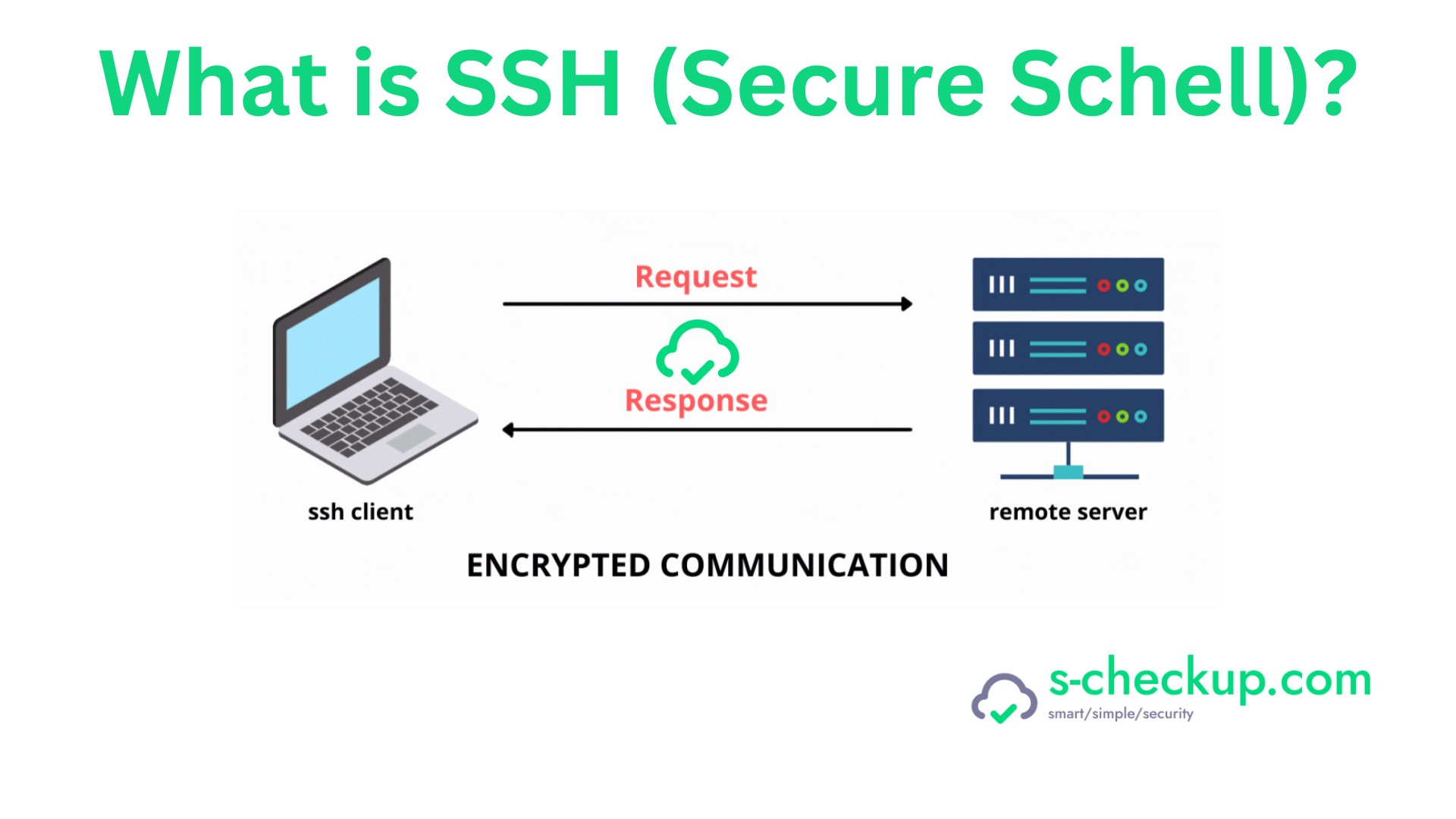
What is Secure Shell (SSH): How does it Enhance Your Network Security
SSH, an acronym for Secure Shell or Secure Socket Shell, is a network protocol designed to provide secure access to a computer over an unsecured network. It offers robust password authentication, public key authentication, and encrypts data communications, making it an essential tool for secure remote access.

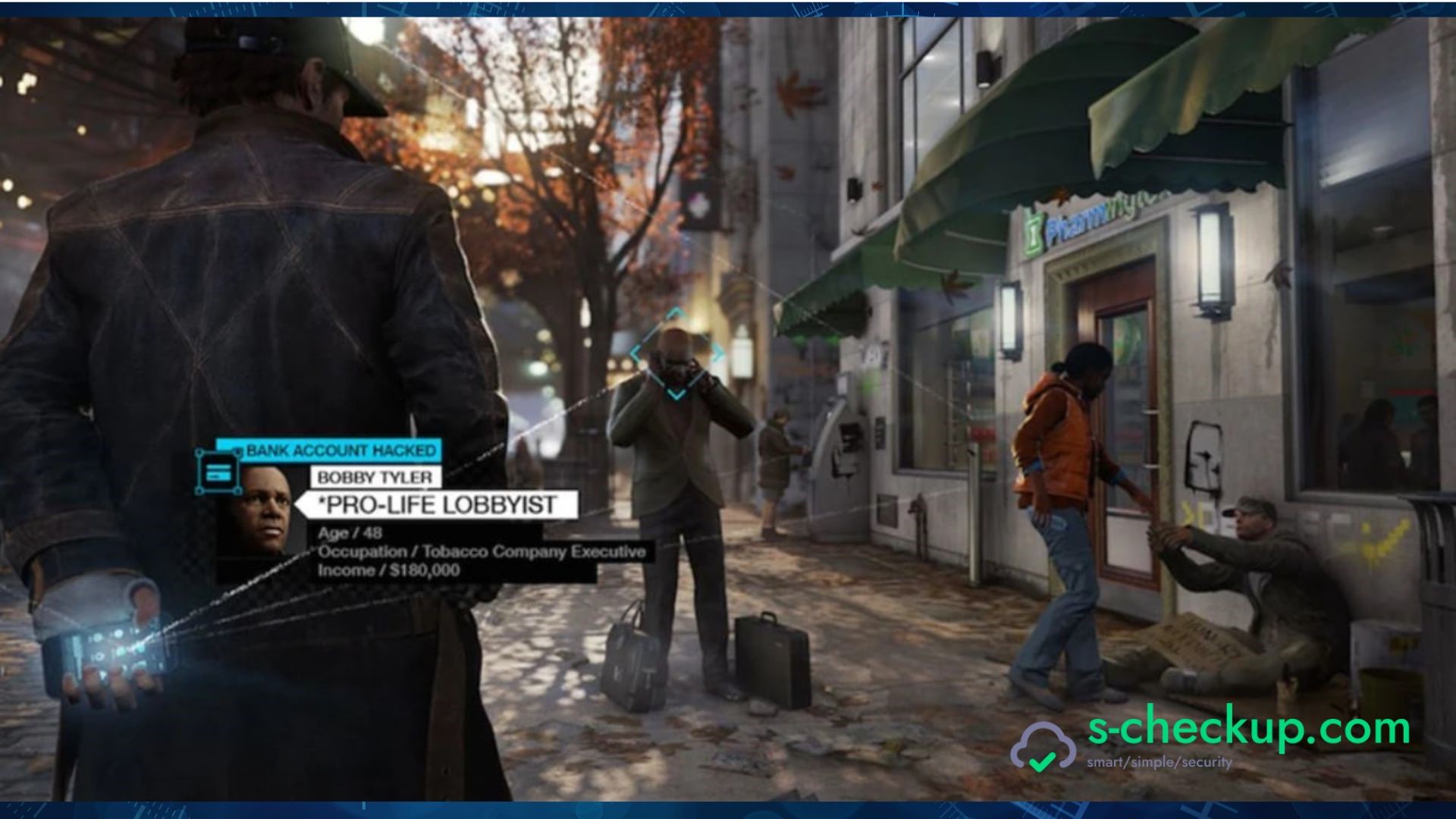
The Ultimate Guide to iPhone Hacking Apps in 2023
Parents worry about their children's online activities, partners may have concerns about fidelity, and employers seek ways to ensure data security and employee productivity. iPhone hacking apps offer a solution to these concerns by providing a means to monitor and protect loved ones or business interests.
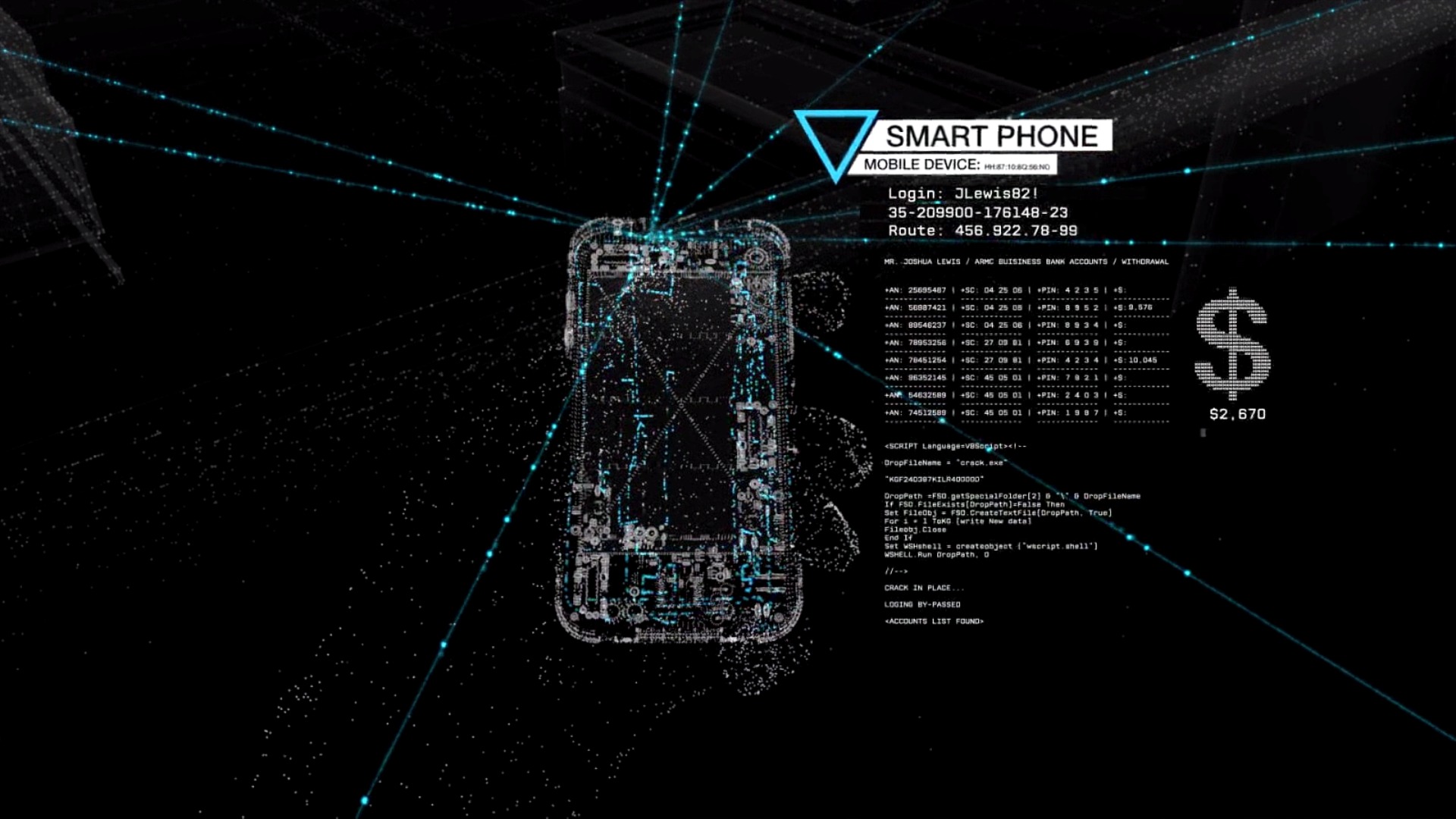
Keeping Website Hacking at Bay with s-checkup
Hardly a day goes by without news of a new hacker attack. Esteemed websites fall prey to malicious code, turning them into launchpads for hacking attacks that distribute malware to unsuspecting visitors' computers. The consequences of website hacking are severe, spanning from data theft to SEO manipulation.
Total Cybercrime cost for Germany in 2023 is 206 billion euro
Bitkom's survey of over 1,000 companies revealed alarming statistics that underscore the gravity of the situation. Around 75% of the surveyed companies reported falling victim to digital attacks in the past year, a slight decrease from the previous year's 84%. While this decline may be seen as a glimmer of hope, it primarily reflects the growing effectiveness of protective measures employed by businesses.

7 Steps to Tell if a Website is Secure
Since 2018, search engines like Google have considered website security as a ranking factor. A secure website enhances its chances of appearing among the top search results. Moreover, having a security certificate instills confidence in your audience, increasing the likelihood of conducting business with your company.

Top 14 Vulnerability Scanners for Cybersecurity Professionals
Vulnerability scanners play a crucial role in cybersecurity, helping organizations identify and address potential weaknesses in their IT infrastructure. These tools are essential for maintaining a robust security posture and protecting sensitive data from malicious actors. With numerous vulnerability scanners available, choosing the right one for your organization can be challenging. In this article, we'll explore the top 14 vulnerability scanners favored by Core Security experts.

Major Cybersecurity Agencies share the 2022 most exploited vulnerabilities
The prevalence of CVE-2018-13379 in the list of most exploited bugs in 2020, 2021, and now in 2022 is a clear indication that organizations have not adequately addressed this security flaw. The vulnerability's impact can be mitigated by applying patches in a timely manner, but many entities have failed to do so, exposing their systems to potential breaches.
Why Vulnerability Scanning is Important
As Russell Miller, CTO of OPSWAT, aptly puts it, "An attacker only needs one vulnerability to gain access." With the number of data breaches increasing year after year, vulnerability scanning becomes a proactive defense mechanism to mitigate potential cyberattacks.

A 10-Point Vulnerability Assessment Checklist to Secure Your Business
Vulnerability Assessment (VA): VA is an automated process that uses tools like web and network security scanners to detect potential vulnerabilities in your systems.
Penetration Testing (PT): PT combines automated tools with manual exploitation of vulnerabilities to simulate real-world attacks and assess the robustness of your defenses.

Pentesting vs Vulnerability Scanning: What's the Difference?
Pentesting vs vulnerability scanning: two very different ways to test your systems for vulnerabilities.
What is vulnerability scanning testing?
Vulnerability scanning plays a crucial role in the field of cybersecurity by helping organizations identify potential security weaknesses and flaws in their systems and software. It is an essential component of a comprehensive vulnerability management program, which aims to safeguard the organization from breaches and the exposure of sensitive data. By conducting vulnerability scans, businesses can assess their security readiness, minimize risks, and enhance their overall cybersecurity posture.

What is Vulnerability Scanning?
Vulnerability scanning is a crucial process in the realm of cybersecurity. It involves identifying security weaknesses and flaws in systems and software, enabling organizations to bolster their defenses against potential breaches and safeguard sensitive data. A comprehensive vulnerability management program incorporates vulnerability scanning as a critical tool to assess security readiness and minimize risks effectively.
Generative AI for hackers: Advancements and Security Challenges with Worm GPT
The Revolutionizing Power of WormGPT
Threat actors leverage advanced AI technologies, including ChatGPT and other similar models, to automate the creation of convincing personalized fake emails. This not only expands the scope of BEC attacks but also enhances their success rate. WormGPT, a black-hat alternative to GPT models, plays a significant role in revolutionizing BEC attacks by offering features such as unlimited character support, chat memory retention, and code formatting.
By exploiting interfaces like ChatGPT with specialized prompts, threat actors manipulate and compromise AI systems to their advantage. The rise of custom AI modules, similar to ChatGPT, developed by cybercriminals further amplifies the complexity of cybersecurity in an AI-driven world. The urgent need for robust AI security measures becomes evident as we delve deeper into the implications of generative AI technology.

Sustainable cybersecurity and vulnerability check for the subdomains and apis
In today's digital landscape, cybersecurity plays a vital role in protecting sensitive information and ensuring the smooth operation of online platforms. With the increasing number of subdomains and APIs being used by organizations, it becomes crucial to establish sustainable cybersecurity measures and conduct regular vulnerability checks to mitigate potential risks. This article explores the significance of sustainable cybersecurity practices and the importance of conducting vulnerability checks for subdomains and APIs.

The Comprehensive Guide to Effective Website Vulnerability Scanning
Understanding Website Vulnerabilities
Website vulnerabilities pose significant risks to the confidentiality, integrity, and availability of your digital assets. Hackers and malicious actors are constantly searching for vulnerabilities that can be exploited to gain unauthorized access or cause harm to your website and its visitors. It is crucial to identify and address these vulnerabilities proactively through regular scanning and security assessments....
How effective are your existent cybersecurity measures?
How effective are your cybersecurity measures on your website?
Let’s say every month your development team comes up with new fixes and updates. While your customers are happy, are you 100% confident that the fixes cover the cybersecurity vulnerabilities?

Understanding PCI DSS in Cybersecurity: Enhancing Cardholder Data Security
The Payment Card Industry (PCI) Data Security Standard (DSS) is an information security standard specifically designed to bolster the security of cardholder data for organizations involved in storing, processing, or transmitting credit card information. By implementing robust controls and measures, PCI DSS aims to minimize vulnerabilities and prevent credit card fraud. Its scope encompasses various entities such as retailers, online payment services, credit card issuers, and providers of payment processing services.